BE INVISIBLE, BE INVINCIBLE
IS YOUR NETWORK SSHepherd® PROTECTED?
CyberArmour is the Asia Strategic Partner of FullArmor Corp, a leader in developing cyber security technology that are licensed to companies like Microsoft, Citrix, NetIQ, Logmein and others. We have been awarded the exclusive rights to distribute the patented SSHepherd® technology for the Asian market.
SSHepherd®
REMOVE THE ATTACK SURFACE
SSHepherd® completely removes the open, listening ports for SSH, RDP, and applications like databases while still maintaining the full access and functionality of those services and applications.
Layered and Complementary Security Practices are Key to Securing Your Network
VPNs and Firewalls are a necessary piece of your perimeter security but this is not enough. Protecting your resources inside the perimeter is a vital piece of your defense.
Preventing unauthorized access to your critical systems, auditing activity during remote access sessions, mitigating the risk of data loss, and good cyber hygiene are key to most security compliance guidelines like NIST, CIS, CERT, and all others.
SSHepherd® enables you to remove the SSH and RDP attack surface
Completely Disable SSH
Close All RDP Listening Ports
Block All Inbound SSH & RDP Traffic
Eliminate SSH & RDP From Port Scans
Remove Threat Of SSH Key Sprawl
Prevent Lateral Movement
End SSH & RDP Brute Force Attacks
Maintain FULL SSH & RDP Capabilities
FEATURES
Control the Access
Removal of the attack surfaces so that only authorized users and applications see the RDP, SSH and application servers
Archive for Audit Compliance
Archives connected sessions from last week, to years in the past to assist in forensic analysis audit compliance
Full Auditing
Logs all activity to your SIEM including who is accessing, when, where from which machine, and their activity
Terminate Sessions Immediately
Continually evaluates and can terminate sessions (manually or automatically) based on rogue behavior
Prevents Lateral Movement
Prevents lateral movement by removing points of ingress and egress
On-Premise and Cloud
Applies to all resources whether on-premise or in the cloud
Easy Deployment
Deploys easily with workflows and DevOps automation tools (Chef, Puppet, Ansible, etc.)
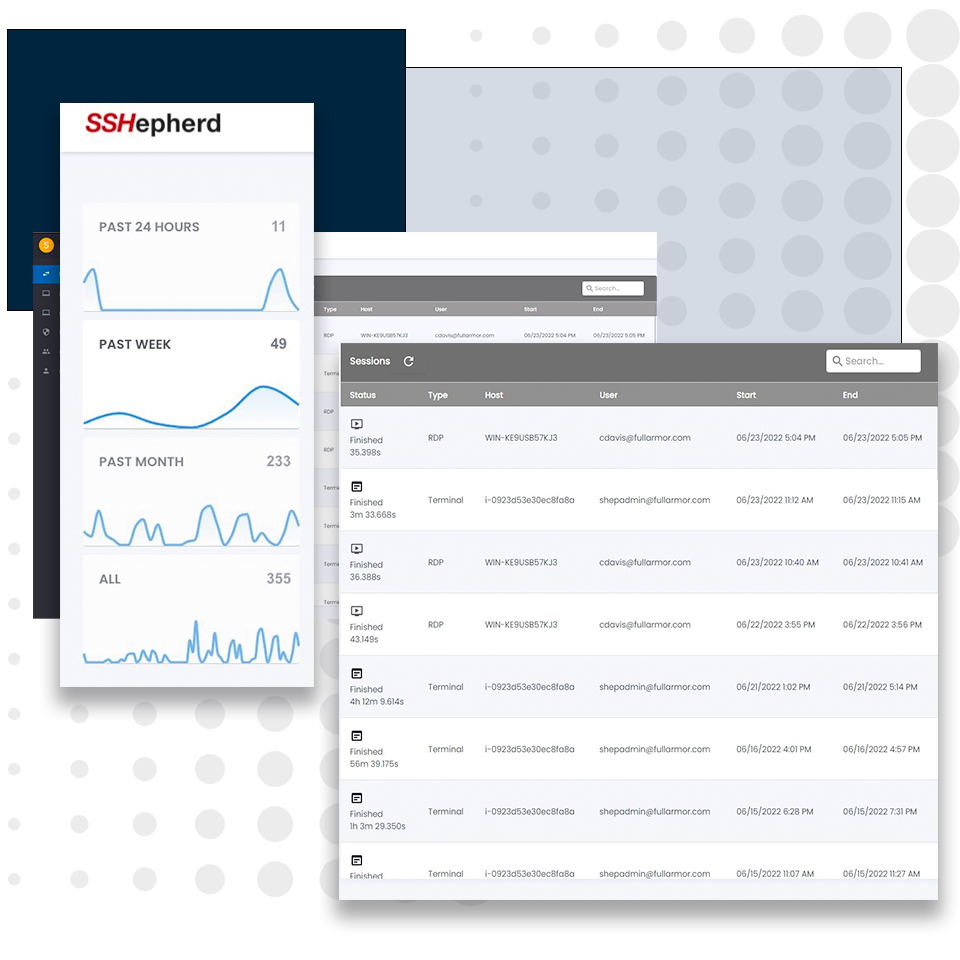
Real-Time Live Look
Live look so you can see the connected sessions and view current operationd
“The share of organizations deploying zero trust grew from 35% in 2021 to 41% in 2022. Organizations that don’t deploy zero trust incurred an average USD $1 million greater breach costs compared to those with zero trust deployed.”
SSHepherd® ZERO TRUST
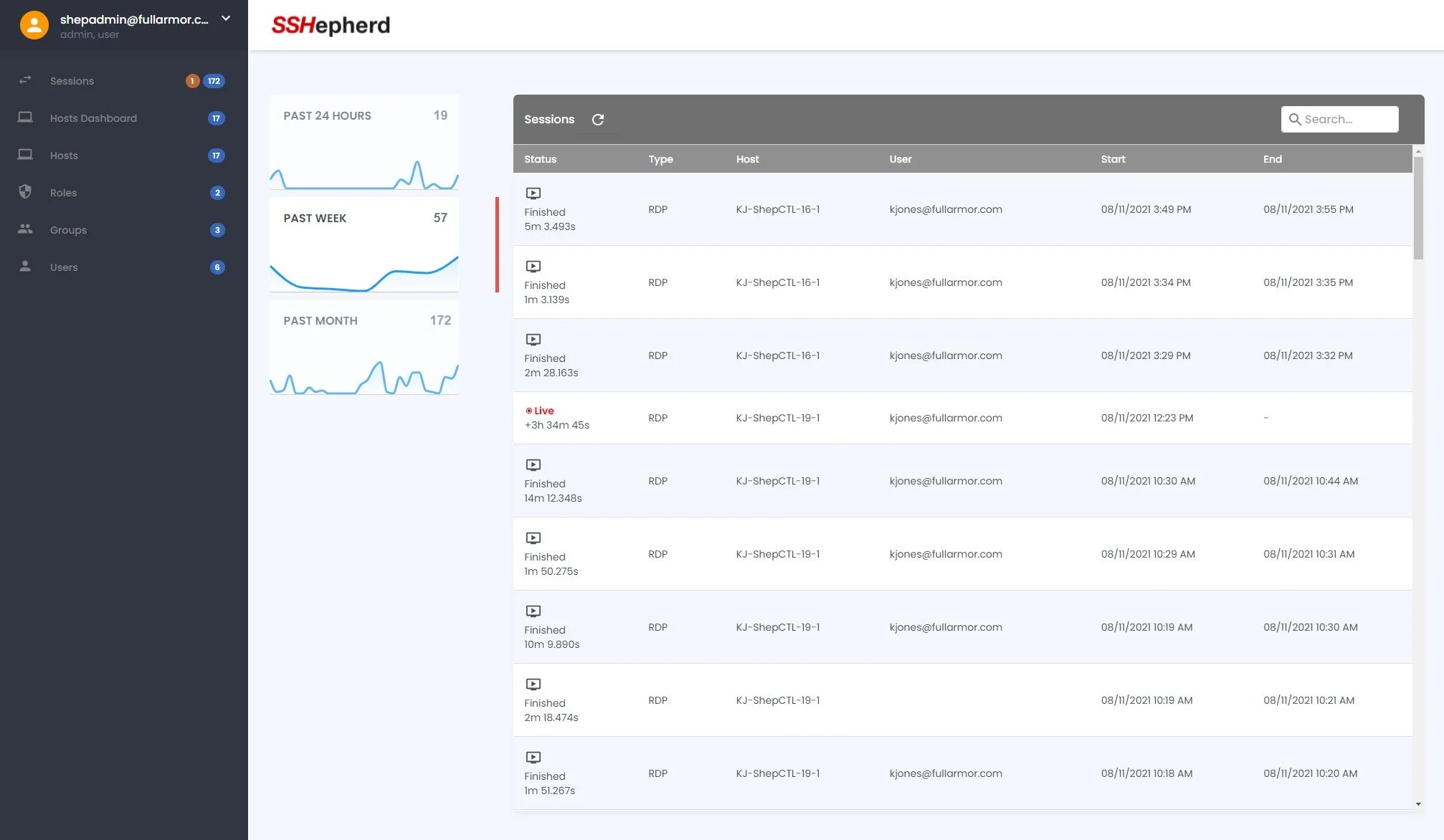
SSHepherd® REMOTE ACCESS AUDITING & LIVE VIEW
Know who has accessed SSH and RDP
Monitoring activity on your systems is a key component of security compliance and audit. Whether that activity is initiated by outside ‘bad actors’ or trusted internal users, knowing what occurs during a connected session is vital to determining whether a breach has occurred and the scope of its impact.
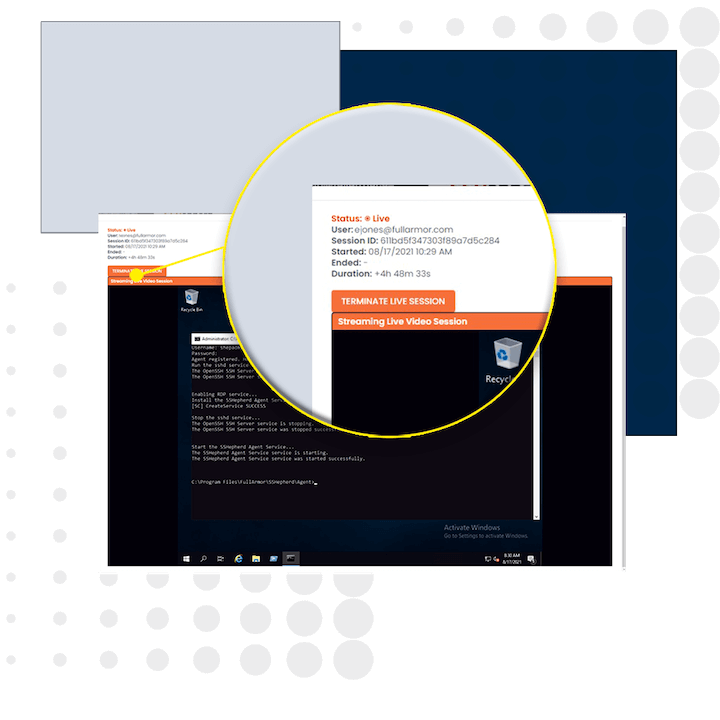
“Kill Switches” to stop unauthorized actions
Built-in “Kill Switches” for termination of managed sessions. The sessions can be terminated during Live View, and through SIEM integration via automation when aberrant behavior is detected and if a user attempts to tamper with the SSHepherd® processes and services.
Comprehensive auditing of remote access sessions
Be prepared to prove the who, what, where and when to auditors. Comprehensive auditing of remote access sessions is a key component of any regulatory compliance guidelines like CIS, NIST, CERT and others.
Full Visibility into Remote Access Sessions
Records the managed RDP and SSH sessions live and streams them to a remote location to prevent removal of audit trails. These recordings provide both a live view of user activity as well as an archive of past sessions for review and assessment by security administrators and auditors.